This is the edited script of a presentation given by Simon Barron at UKSG 41st Annual Conference and Exhibition in Glasgow, UK on 2018-04-09 and 2018-04-10. It has been edited to incorporate the accompanying presentation into the text and to insert additional detail and quotes. Thanks to Matt Borg for asking me to present and thanks to the UKSG organisers for their hard work.
1.0: art of revolt
Surrealism has been called “the art of revolt” (Sélavy, 2018). The artistic movements, Dadaism and Surrealism, developed in the early 20th Century as reactions to the dominant bourgeois social norms and the growth of capitalism both of which were leading to economic recessions and war. A range of artists, poets, and writers came together in 1916 in Switzerland to create the Dada Manifesto. This manifesto emphasises the intense connection that the artists saw between art and life. Their subsequent art interrogated the existing bourgeois value systems that existed in the art world at the time. We see this in Marcel Duchamp’s 1917 piece, Fountain, which questions the very idea of what a work of art can be.
Surrealism emerged out of Dadaism and distinguishes itself by its explicit focus on politics. Whereas Dada focused on the meaning of ‘art’, Surrealism focused on the inner workings of the mind and the irrational in ways that critiqued capitalism and Western society. By blurring the lines between dream and reality, the irrational and the rational, the Surrealists demonstrated the arbitrariness of the rules and authorities governing capitalist society. The intention behind Surrealist art and Surrealist cinema was to shock the audience out of complacency. The first Surrealist film, Un chien Andalou, by Luis Buñuel and Salvador Dalí was released in 1929.
It was viscerally shocking for audiences of the time raising questions about the nature of desire and violence barely held back by ineffective and stifling bourgeois societal norms. Buñuel and Dalí’s second collaboration, L’age d’or, was released in 1930 and was even more explicit in its criticism of the upper class, organised religion, and capitalist society. Following a campaign by a right-wing group in France, the film was banned and repressed until 1979.
Surrealist artists and directors had no political power. They had no means of changing society and addressing the social inequalities that they saw all around them perpetuated by capitalism and the upper classes’ relentless pursuit of capital. Surrealism – their ‘art of revolt’ – was the only way that they could express themselves against a monolithic political system that was unreceptive to their ideas and their very mode of expression for those ideas. It was an art of desperation, of irrational yearning, of passion, and of expressing themselves at any cost in the only way that they could.
In 2018, we face an even more monolithic political and economic system. Capitalism evolved into global neoliberalism and has reached a point where almost everything is subject to its processes of marketisation. Crucially for libraries, archives, and other information providers, information is increasingly commodified and marketised. Neoliberal practice turns information and knowledge into commodities: products that can be bought and sold. It’s a system of political economy that conceives of information and knowledge as products that can be transferred or exchanged in market transactions like other objects. Closing off information, paywalling it, and restricting access to it is part of neoliberalism’s ideology to consolidate power for those who claim to own information.
Like the Surrealists, libraries don’t have power under capitalism and we have to push back against neoliberalism in the small ways that are available to us. As a library systems worker in UK Higher Education, I can use open-licensing as a tool to push back against the commodification of information. I want to talk today about open-licensing and the benefits of open-licensing for libraries and other information providers. I’ll particularly focus on open-source licensing of software.
1.1: library systems
Library systems are the lifeblood of a modern library. Whether a small public or corporate library or the national library of a country, that library uses specialist library software to help run the library. Circulation of books, acquisitions of serials, security and access control, analytics and reporting, electronic resources management, reading list management, institutional repositories, research data management repositories, digital asset management, loanable laptops or mobile devices. All these functions depend on library systems which, if functioning properly, go unnoticed day-to-day. Modern librarianship could not exist without library systems.
With such a foundational role in the everyday running of libraries, it’s curious that there is such a lack of critical scrutiny directed towards these systems. Journal articles, conference presentations, and blog posts about systems librarianship tend to focus on practical projects and how-to guides. Discussions at library systems conferences tend to focus on how our systems will accommodate the latest trendy fad – linked data or Bibframe or RDF – and on the difficulties of negotiating with the corporate suppliers of library systems. There is much less discussion of the ethical issues surrounding managing computer systems, having control over so much of the library’s functioning, and having direct access to so much of the library’s data. There is little discussion of how a systems librarian should act to balance the best interests of their users, the library as a whole, and the requirements of social justice and decency.
I advocate an approach that Preater and I (2018) call ‘critical systems librarianship’. This approach is based in critical theory: a school of thought that originated with the thinkers of the Frankfurt School and applies a holistic approach to critiquing institutions and processes by recognising them as embedded within larger power structures in culture and society. Critical systems librarianship is about acknowledging power relations and structural inequalities within libraries, an awareness that we practice within the confines of white supremacist capitalist patriarchy (hooks, 2009), and an active approach to addressing social justice issues in our library systems work (Barron & Preater, 2018, p. 88). Following Caswell’s (2018, p.161) approach to critical pedagogy in archival studies, critical systems librarianship empowers practitioners to simultaneously critique, imagine, and act. That’s what I intend to do today starting with critiquing current practices for library systems.
2.0: critique
From the first automation of catalogues and library management, library systems have tended to be proprietary or closed-source software and they tend to be provided by library software vendors. These are specialist companies that libraries pay subscriptions to for them to provide and run the software. Increasingly, this isn’t a matter of the companies passing the software to libraries to install and run themselves but of software-as-a-service which involves the companies running the software on their own servers and allowing libraries to access it through web browsers.
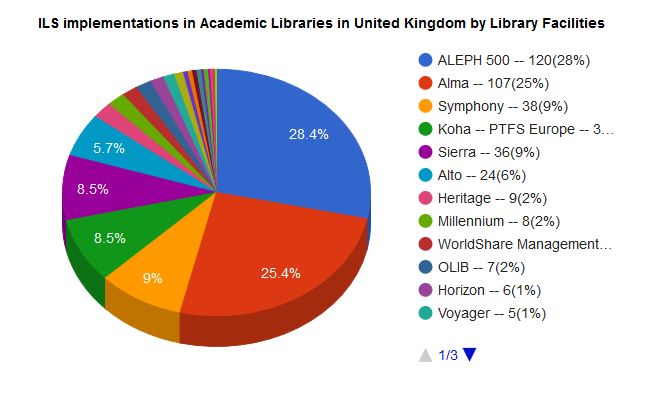
If we look at library management system implementations in academic libraries in the UK, then we see the vast majority use proprietary systems with a huge chunk using a system that is only provided as a cloud-hosted platform: Ex Libris Alma (Breeding, 2018a).
Similarly for public libraries in the UK, we see huge use of proprietary systems provided by corporate vendors (Breeding, 2018b).
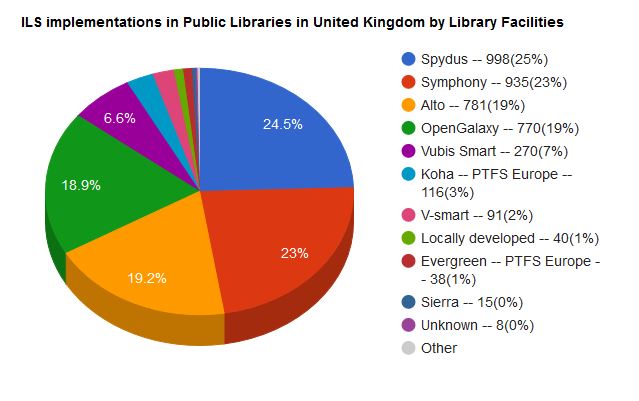
Among the biggest vendors in library systems are OCLC, Ebsco, SirsiDynix, Innovative Interfaces Inc., Ex Libris, and ProQuest (which owns Ex Libris).
Considering the power relations between entities is an important aspect of critical systems librarianship. The relationship between libraries and library systems vendors is built on imbalanced power relations. ‘Power’ is used in the sense of Foucault (1975/1991) who understood power not simply as direct physical violence or the threat of violence but as subtle methods of coercion and control that one party operates over another. In the West, the state reserves violence and the threat of violence only for exceptional cases: Western states generally maintain power through news propaganda and education, through surveillance and legislation, through control over capital, and through the bourgeois societal norms that the Surrealists were protesting against. We need to scrutinise these kinds of power relations between the library and its users and between libraries and library systems vendors. Only by doing this can we properly consider how to redress the balance of uneven power relations.
We’re well aware of scholarly publishers who exercise power over academic researchers. Library workers, tend to say the name “Elsevier”, for example, through gritted teeth. But there’s less discussion of the power that systems vendors operate over libraries as part of what Popowich (2018, p. 57) calls the “oppressive and parasitic library technology vendor ecosystem of today”. Library software vendors offer licenses for software as restrictive as those for scholarly publishing with contracts that include nondisclosure agreements on costs of the software, no ability to retrieve one’s own data, no ownership rights over any custom modifications that are made to the software. These restrictions form a monopolising practice as they restrict the ability of libraries to choose other systems or migrate to other systems. Rather than challenging these business practices, libraries are continuing to buy software licenses and support contracts from these companies to keep their libraries running.
As Galvan (2016) writes, “vendors now have so much power in libraries their products show up in our job descriptions, as though systems don’t migrate or change.” Galvan provides several examples of how software vendors exercise power over libraries and, in so doing, further their own commercial interests at the expense of the ethical interests of the library. Her examples give two major ways that suppliers exercise power: through systems design and through library staff labour and attitudes.
Using the example of Ex Libris Alma, Galvan demonstrates how system design constrains the practice of librarianship. Alma—and specifically Alma Analytics, the system’s reporting module—was consciously designed to present data and analytics based on what Ex Libris developers thought would be valuable for the library staff user rather than what the library staff user will actually find valuable. Similarly, Galvan argues that library discovery systems are designed to look like Google but to act like Amazon. These commercial discovery layers “[prioritize] the results from certain content over others. It’s in Ex Libris’ best interest to prioritize ProQuest databases, just like EDS prioritizes EBSCO products.”
Reidsma (2016) has also written about the bias in commercial library discovery layers. In his study of algorithmic bias in ProQuest’s Summon library discovery system, Reidsma discovered how not only would Summon present inappropriate Topic Explorer results to the user but it did so because Summon was designed to add Wikipedia to the Summon index rather than match against Wikipedia’s API. Through attempting to centralise control of their product, ProQuest compromised the quality of search results presented to the user. Reidsma’s study also suggests that the bias in the algorithm reflects the biases of wider society against marginalised communities: there are specific biases against women, the LGBT community, Islam, and mental illness. These systems are therefore complicit in the perpetuation of societal inequalities which reinscribe the privilege of those who control and exercise power. Simply put, the imbalanced power relations in systems librarianship reflect those of society.
The very structure of modern library systems and the software-as-a-service infrastructure is designed to consolidate the power of the vendors. Software-as-a-service or cloud-hosting is a software infrastructure in which, rather than providing software to install on a server under your control, a supplier runs the software for you on a remote server which you access over the internet. This is the model of much contemporary software offered at zero monetary cost, such as Google’s suite of products. Cloud computing comes with a “Faustian bargain” (Rogaway, 2015), relieving systems librarians of the need to maintain servers, install updates, and deal with technical issues themselves but also shifting control over those systems to the supplier.
In library systems, cloud-hosting often uses a multi-tenant architecture in which several versions of the same piece of software all run on the same server. This saves the supplier from running a server per customer and simplifies software development, testing, and change control. A multi-tenant server has the same structure as Bentham’s Panopticon: a prison in which the guards can see every prisoner but the prisoner cannot see the guards, cannot know when they are being monitored, and cannot see the other prisoners around them. On a multi-tenant server, the supplier can monitor everything that the customer does but the customer cannot see what the supplier does, what the supplier is monitoring, and which other customers share that server. The prisoner in the Panopticon must assume they are being monitored at all times and behave accordingly. In Doolin’s (1998) terms,
“the development of information systems to monitor and scrutinize particular organizational activities facilitates control by making individuals within an organization both calculable and calculating with respect to their own actions. This invokes the notion of an electronic panopticon, in which organizational participants are enlisted in their own control through their belief that they are subject to constant surveillance[.]”
Discussing the tendency in librarianship to view technology as value-less or politically neutral, Popowich writes:
“Our tendency to see technological change as something outside our professional and social relationships has made up primarily reactive, always trying to catch up, rather than critically interrogating technological change, which might allow us to regain some agency and control over that process.” (Popowich, 2018, p. 50)
As it stands, technological change is imposed on us because vendors have power over us. Vendors provide us with software updates or tell us that their roadmap is pushing us to their new piece of software or our old processes will no longer be supported following a software update. Over the past few years, as Ex Libris has phased out support of it’s old Aleph library management system (and even older Voyager library management system), the vast majority of old Aleph customers simply moved to Ex Libris’ successor product, Alma. Technological change was driven by the system and by the vendor, not by the libraries.
As libraries, we are given these updates by our software vendors and yet, far from addressing our long-standing and legitimate criticisms of the old software, the new software tends to only introduce new issues and consolidate existing issues. Despite change being driven by the vendors and passively accepted by libraries on the understanding that new products will fix the problems with the old products, the products that they produce are not getting any better. In all these examples, the power relations are skewed in favour of the library systems suppliers. Ethical systems librarians want the best possible software to run our libraries and meet the needs of our users. Software companies want to produce the minimum viable product to maximise their profits. These two goals are fundamentally incompatible. “It is increasingly clear that our interests, as software-using humans, are diverging from the interests of software companies.” (Kriss, 2016) Regaining autonomy over systems is an ethical imperative for libraries because we cannot effectively fulfill the needs of our users or provide the best possible service while shackled to library systems that do not and cannot work for us.
3.0: imagine
3.1: openness
So what can we do to resist companies that exercise power over us? If art was the Surrealists’ medium for expression of dissent, what medium is available for libraries and information providers? I want to discuss openness as a core ethical component of librarianship and a route to this resistance. Fundamentally, libraries provide information: in the traditional view of librarians as gatekeepers, libraries open information to the world providing access to all. In practice, libraries strive to open themselves to all who meet their criteria for users and open information as far as possible within the parameters of copyright law and the restrictions imposed by commercial organisations. Librarianship is about providing information as a public good. This is enshrined in Cilip’s Code of Professional Practice (2012) in clauses D.1. and D.2 with reference to the public good and promoting equitable access to information. The American Library Association’s Core Values are even stronger saying that:
“[a]ll information resources that are provided directly or indirectly by the library, regardless of technology, format, or methods of delivery, should be readily, equally, and equitably accessible to all library users […] [L]ibraries are an essential public good and are fundamental institutions in democratic societies” (ALA Council, 2004).
Implied here is the view of information as a commons: a publicly shared resource held in common by the public. Information has distinct ontological characteristics that distinguish it from commodities like wheat or PlayStation 4s. Information can be shared without losing or damaging the original object, information can be transferred with the need of exchange of capital. If I give you my PlayStation 4, then I no longer have my PlayStation 4. Whereas if I give you the fundamental insights of Marxist economic theory, I do not thereby lose those insights myself. Information does not belong to anyone: it belongs to everyone.
“[S]cholarly information and knowledge, primarily articulated through scholarly communications, is inherently a commons.” (Lawson, Sanders, & Smith, 2015)
Neoliberal capitalism, on the other hand, views information as any other commodity to be bought or sold. Neoliberalism pushes against the view of information of commons through applying copyright law to information and by restricting access to information. Companies like publishing companies can create silos of information which require payment and subscriptions to access. Social media sites like Twitter and LinkedIn commodify the personal data of their users and sell that personal data to advertisers who can use it to create personalised advertisements.
“Private companies generate profits from the commodification of personal data, collecting and selling in return for using “free” services (Richards, 2013). The rapid commercialisation of the internet from 1995 onwards was crucial in consolidating the notion that information is a commodity (Lyon, 2015). Increasingly our personal data has become a commodity for large corporations to derive profit.” (Clark, 2016)
3.2: open licensing
The commodification of information is part of neoliberalism: a monolithic political and economic system. Like the Surrealists, we can resist this in small ways. Open licensing is one way to achieve the theoretical ideal of openness in practice by applying rules to information that aren’t the default rules of copyright. In ethics, we talk about openness in the abstract but ‘open’ also has a precise definition and this definition is given by open licensing. A license is a document that specifies what can and cannot be done with a work or piece of content. It precisely outlines the permissions and restrictions on that content. So an open license is a license which grants permission for people other than the content-creator to access, use, re-use, or redistribute a work with few or no restrictions. For either a work or a license to be open, they must meet the conditions of the Open Definition 2.1 (Open Knowledge International).
There’s been a surge in library support of open licensing of documents and in particular scholarly research over the past few years. Higher Education libraries in the UK have encouraged their institutions’ researchers to publish their scholarly research under open licenses in order to avoid giving control or copyright over to predatory publishing companies. You may be familiar with the Creative Commons series of licenses which can apply to text documents, audio, images, video, etc. If you’re publishing, then you should be publishing using an open-access license.
Open-source licenses are licenses that apply to source code for software. Software is made of source code: underlying computer code that determines how software works. Like Creative Commons licenses, open-source licenses specify what can and cannot be done with source code. They usually specify various permissions around distribution, access, attribution, editing the code, and redistributing derivations of the code. An open-source license is one that complies with the Open Source Definition provided by the Open Source Initiative (2007). Some functionally similar open-source licenses include the Apache License 2.0, the GNU General Public License version 3.0, the MIT License, the Mozilla Public License 2.0 and the self-explanatory WTFPL (Do What The Fuck You Want To Public License). It’s worth noting that the Open Source Initiative does not endorse the use of the last license for licensing source code because it’s basically the same as releasing the code to the public domain (Open Source Initiative, 2009).
Open-source software that you may know includes Mozilla Firefox, Linux operating systems, MySQL, Android operating systems. This is in contrast to proprietary software products like Microsoft Windows, Microsoft Word, Microsoft Excel, Internet Explorer, Google Chrome, Adobe Photoshop, iTunes, Apple’s operating systems.
I want to emphasise a couple of things: open-source software has nothing to do with the cost of that software. Proprietary software can be free like Google Chrome or MarcEdit and open-source software can be paid for. Open-source software also has nothing to do with who distributes a piece of software. A large company can release open-source software, a community of coders can release open-source software, a lone developer can release open-source software. Microsoft, one of the biggest tech companies in the world, recently released a version of Visual Studio called Visual Studio Code as open-source. Red Hat is a huge software company that sells open-source software and has built its business on it.
In terms of library systems, there are many mature open-source products which represent viable alternatives to closed-source systems. Koha, Evergreen, Invenio, and the upcoming Folio are all viable library management systems; VuFind and Blacklight are catalogue and discovery systems; EPrints and DSpace are institutional repository programs; SobekCM is a digital asset management system.
3.3: adoption of open-access
Over the past decade, libraries have widely adopted and advocated for open licensing of scholarly research. Higher Education libraries in the UK have built up open-access teams and members of staff specifically to facilitate publishing research outputs under open licensing and encourage researchers to avoid giving control or copyright over to publishing companies. Library workers publish their own research outputs in open-access journals and deposit post-print versions of book chapters and articles in institutional repositories. We’ve also seen large-scale resistance to particularly egregious restrictive publishing companies like Elsevier.
But this drive for openness in libraries has been piecemeal. Rather than embedding openness throughout library processes, libraries have developed separate teams and roles to deal with open-access and research data management. The adoption of an open ethos is confined to the area of scholarly publishing and research output rather than interrogating other, more traditional, library processes like acquisitions, cataloguing, and systems.
This is partly because, certainly in UK Higher Education libraries, the approach to open access was driven by external pressure from outside librarianship. Our practice was driven by the requirements of the REF and the TEF and enforcing institutional compliance with open licensing as part of those mandates. As Lawson (2018) explained in their recent talk for RLUK, the UK Coalition Government pushed for the REF and advocated for openness in government and public sector organisations as a means to allow private capital to exploit public resources. The OA ecosystem consequently looks very similar to the subscription ecosystem it was supposed to replace (Earney, 2018). Rather than adopting openness because of internal critique and a drive for ethical practice or social justice, we adopted openness specifically in the area of scholarly publishing and we did this because we were told to.
This explains why, despite having the same ethical basis – the open sharing of information – open-access licensing has taken off in libraries and open-source licensing has not. Given this shared ethical basis, it’s unsurprising that open-source systems have been used to enable open-access in libraries with systems like EPrints, DSpace, and Open Journal Systems all widely used and with new systems like Janeway continuing to be developed. But adoption of open-source in other areas of the library has been scant. We’ve failed to scrutinise the licensing of our library systems software because there’s been no external pressure driving us to do so.
3.4: openwashing
Library systems vendors, however, have taken advantage of our stated ethics of openness. Capitalism deals with threats by co-opting them, diluting their message, and presenting them back in a more palatable form. We see this with Surrealist film during the 20th Century. As I explained, Surrealism is an inherently political art movement: it is a subversion of status quo norms and a reaction to the injustices of capitalism. Norris (2007) discusses how, after the first Surrealist films appeared, American animation studios co-opted the imagery of Surrealism for their cartoons, diluting the images and robbing them of their political context. The Fleischer brothers used Surrealist images in the dreamy atmosphere of the Betty Boop cartoons and, at Warner Brothers, Robert Clampett adopted Surrealist tropes in his depiction of dreamworlds in Porky Pig cartoons.
We also see the mainstream co-opting Surrealist imagery in the films of Alfred Hitchcock particularly his 1945 film, Spellbound, to which Salvador Dalí contributed designs.
In the American animations and Hitchcock’s mainstream thrillers, Surrealism is adopted as an aesthetic rather than a spirit and robbed of its emotive power to shock audiences and say something revolutionary against capitalism.
In the same way, library systems vendors co-opt the language of openness and dilute it of its power to challenge capital. Many library systems make a virtue in their marketing materials of being ‘open’, ‘breaking down silos’, or ‘empowering libraries’ in order to appeal to libraries’ principles of openness. But these claims are, in many cases, openwashing: claiming openness while actually distributing proprietary or closed software (Watters, 2012).
Innovative Interfaces Inc., for example, call their vision for libraries the “Open Library Experience (OLX)” (Innovative, 2016a) and say that “With Sierra [their library services platform product], the library is OPEN.” (Innovative, 2016b). Sierra is not an open-source licensed product and Innovative’s documentation on its products is not open-access. These terms are used to mislead. These products are not open in any meaningful sense of the term. We need to be wary of vendors co-opting our language and our professional ethics to sell their products and dilute our ethics’ revolutionary power.
3.5: advantages of open-source
I’ve been discussing the advantages of open licensing and open-source library systems throughout this piece. Those advantages have been based on ideas of ethical practice, social justice, and explicitly resisting neoliberalism. But I’m aware that we operate within white supremacist capitalist patriarchy. Ethical and social justice advantages are not enough to make the case for open-source systems to management. Those kinds of arguments are not politically acceptable or sufficiently within capitalism’s preferred discourse of ‘rationality’. The Surrealists placed their artwork outside the sphere of rationality and logic precisely because capitalism uses the discourse of Western rationality to justify itself and to restrict the bounds of acceptable thought. Within neoliberal structures, we don’t have the luxury of using ethics to justify our decisions. So I want to briefly adopt the language of neoliberalism to think about some advantages to open-source library systems that are based in practicality and efficiency. In the words of Adrienne Rich (1971):
“knowledge of the oppressor
this is the oppressor’s languageyet I need it to talk to you”
3.5.1: reliability
When the bourgeoisie failed to understand Surrealism, they labelled it impossible to understand, too obtuse, too intellectual. When neoliberal capital resists openness and open licensing, it represents it as unreliable or inefficient. Open-source systems are often unfairly represented as the products of hackers tinkering in their basements and then releasing the code on to the Deep Web. While it’s true that open-source software can be less convenient to implement in some ways than proprietary software, it’s simply untrue that it’s unreliable. Open-source software is among the most widely used and most reliable software in the world: the Apache HTTP server serves approximately 46% of all active websites and 43% of the top one million websites in the world (Netcraft, 2016); MySQL is a central component of the LAMP stack and used as part of the backend for websites and services like Google (Claburn, 2007), Facebook (Callaghan, 2010), Twitter (Cole, 2011), and YouTube (Oracle); the Android operating system has been the best-selling smartphone operating system since 2011.
Open-source software is also more reliable in terms of security and data privacy. “In the cryptography world, we consider open source necessary for good security; we have for decades. Public security is always more secure than proprietary security. It’s true for cryptographic algorithms, security protocols, and security source code. For us, open source isn’t just a business model; it’s smart engineering practice.” (Schneier, 1999) Because the code is open, it means more people and a wider range of people can scrutinise it for security flaws. So holes tend to be found and patched more quickly than with proprietary software. If Ex Libris Alma has a security flaw, for example, then we wouldn’t even know it existed until Ex Libris’ developers discovered it and chose to tell us.
3.5.2: customisability
Proprietary software tends to be limited in the extent to which systems librarians can customise it. Logos, colours, and terminology can be customised but for substantive page designs, adding new pages, or adding bespoke new features, the systems are too locked down. So we end up with homogenous systems design like library catalogue and discovery systems which, for UK HEI libraries, all tend to look alike. Open-source software is, by its nature, more customisable. Because you can edit the code, you can heavily customise the HTML for display, you can write new bespoke features, and you can change the way that processes work to suit your users. Every library is unique: they have unique holdings, unique metadata, and unique users. A search solution that works for one library may not work for another. I believe that libraries should embrace their diversity and build systems that reflect that diversity. The only way to achieve that is with systems that aren’t controlled by library systems vendors.
3.5.3: extensibility and interoperability
Full access to the database of open-source software provides many more opportunities for extending and integrating the software. It’s a lot easier to get data out of a system that you can fully access than software where you are restricted by a vendor. At Soas Library, we use OLE, an open-source library management system built by a community of librarians and developers. We have full access to the underlying MySQL database which means that at any time, I can retrieve any piece of data from the system that I want from patron fines details to full Marc records. Open-source also makes it easy to send full data like bibliographic data to other libraries or to union catalogues: we can build scripts to export full Marc files in a variety of formats knowing that the system isn’t leaving any data behind as tends to happen with exports from closed-source library systems.
3.5.4: cost
I won’t overemphasise the cost benefits of open-source because it comes with huge caveats. If resources are allocated to the right places, then open-source can be cheaper than closed-source. Open-source tends not to have the extortionate license fee costs that proprietary software has and, since maintenance and development can be done in-house, you can also avoid support costs. If you work with one of the many companies who cloud-host open-source library systems, you can avoid paying for your own server and network infrastructure. However there can be initial resource outlay involved in building up a team of technical staff with the skills and knowledge to work on open-source or contracting a development team to do this work for you. You could potentially spend more up-front on open-source than you would on equivalent proprietary software. The difference is that after the initial cost investment in staff or infrastructure for open-source, those resources can be reused at low-cost to expand your systems and develop existing systems.
3.6: disadvantages of open-source
Open-source software isn’t perfect. There are very strong ethical and practical advantages to open-source as I’ve discussed but there are some practical disadvantages to open-source that mean it isn’t always suitable for an organisation particularly an organisation unable or unwilling to commit resources to initial deployment.
3.6.1: complexity
I tend to frame the difference between open-source and closed-source as a matter of control vs. convenience. When you use open-source, you have control over the system: you’re able to customise it, build new features on top of it, access your full data. But it can be less convenient to install and deploy. With some products, you don’t have support from a vendor. Instead you’re relying on the good faith of a community of users and developers.
3.6.2: toxic masculinity
From a social justice perspective, open-source development communities have been subject to criticism for their cultures of toxic masculinity and deference to white cisgender male leaders at the expense of gender and race equality. Jacob Appelbaum, a developer for the Tor Project, resigned from the project in 2016 following accusations of widespread sexual misconduct (Blue, 2016). Richard Stallman, the founder of the free software movement and several foundational pieces of open-source software, has been accused of misogyny and sympathy for child abusers (Geek Feminism Wiki). In its deference towards the authority of white men, the open-source community reproduces and perpetuates the social inequalities of white supremacist capitalist patriarchy.
3.6.3: distribution of labour
Distribution of labour. There are also concerns about the distribution of labor in open-source development. In their study of commits to code repositories for Apache projects, Chełkowski et al. (2016) found inequalities in the distribution of labor with a very small minority of developers producing the majority of commits with a similar power law distribution to other online communities. They argue the claimed benefits of collaboration in open-source development are over-emphasised. Similarly, in relation to open educational resources, Neary and Winn (2012, p. 409) argue that uncritically praising openness and the information commons can erode recognition of the labor involved in the production of open resources (or open-source software): “[t]he reification of ‘the commons’ as a site of non-scarce, replicable and accessible educational resources is to mistake the freedom of things for the freedom of labor.” The valuing of unpaid labor in open-source development also contributes to the inequality issues discussed above: people in marginalised communities tend to have less free time and social capital to expend on unpaid contributions to projects (Dryden, 2013). This contributes to a lack of diversity in open-source development.
4.0: act
We’ve discussed the ethics of open-source software and open-access licensing in libraries. We’ve discussed some practical advantages and some disadvantages. What can you do in your practice to support and promote open-source software in libraries?
Talk to your technical staff. Involve your systems teams in procurement processes and development decisions. Being a senior manager or a director does not make you an expert on systems and what will work for your library. Talk to your systems experts and your subject matter experts and get their opinions. If there are complaints about your existing library systems, don’t dismiss them. Don’t just assume that people are having a moan. Take them seriously and look at what software can overcome those issues.
Use open-source software. Even if you’re not replacing your library systems, you can use and support open-source software in place of proprietary software that you may already be using (Barron, 2016). Get over your fear of unfamiliar software. In my experience, open-source versions of popular software often work better than proprietary market leaders.
Read the contracts or licenses for your existing library systems. Or ask your senior management team about them. Interrogate anything that seems off or that seems to give the vendor too much power. Think about how much access the vendor has to your data. Ask your users if they’re aware that a company has that much access to their data.
Talk to others about open-source. Start the conversation in libraries. If someone is a supporter of open-licensing in publishing, ask them if they support open-licensing in software. If you’re a member of Cilip, push them to take a stance on open-source in libraries. As far as I’m aware, Cilip have no guidance on ethical procurement of library systems or best practices in systems librarianship.
5.0: systems of revolt
Open-licensing is not a panacea to openness in libraries or to resisting the commodification of information (Lawson, 2018). Open-access and open-source won’t fix our broken libraries, won’t bring in more revenue for libraries, won’t stop monopolistic library systems vendors or predatory publishers.
But open-licensing is a small way to resist the encroachment of neoliberalism and its commodification of information. It’s a small way to say, “Yes, I want to share this. I want the world to see this.” It’s a way to share and give that knowledge to someone else. Like Surrealism, it’s a small way to effect political change and a way to express ourselves in the way that we want to express ourselves against an increasingly commodified and capitalist society. The Surrealists resisted using art and cinema and artistic expression. We can resist using licensing, control over our own systems, and a spirit of openness.
6.0: references
L’age d’or, 1930. Directed by Luis Buñuel. Paris: Vicomte de Noailles.
ALA Council, 2004. ‘Core Values of Librarianship’. Accessed 2018-03-21 at http://www.ala.org/advocacy/intfreedom/corevalues
Barron, S., 2016. ‘11 open-source alternatives’, undaimonia. Accessed 2018-04-12 at https://simonxix.wordpress.com/2016/01/07/open-source-listicle/
Barron, S. and Preater, A. J., 2018. ‘Critical Systems Librarianship.’ in: Nicholson, K. J. and Seale, M., eds., 2018. The politics of theory and the practice of critical librarianship. Sacramento: Library Juice Press, pp. 87-113.
Blue, V., 2016. ‘“But he does good work.”’ Medium. Accessed 2018-04-12 at https://medium.com/@violetblue/but-he-does-good-work-6710df9d9029
Breeding M., 2018a. ‘Market share report: Academic Libraries in United Kingdom’, Library technology guides. Accessed 2018-04-12 at https://librarytechnology.org/products/marketshare.pl
Breeding M., 2018b. ‘Market share report: Public Libraries in United Kingdom’, Library technology guides. Accessed 2018-04-12 at https://librarytechnology.org/products/marketshare.pl
Callaghan, M., 2010. ‘MySQL at Facebook’, presentation delivered on 2010-04-13 at O’Reilly MySQL Conference & Expo 2010 in Santa Clara, USA. Accessed 2018-04-12 at https://www.youtube.com/watch?v=Zofzid6xIZ4
Caswell, M., 2018. ‘Envisioning a Critical Archival Pedagogy.’ in: Nicholson, K. J. and Seale, M., eds., 2018. The politics of theory and the practice of critical librarianship. Sacramento: Library Juice Press, pp. 159-166.
Chełkowski, T., Gloor, P., and Jemielniak, D., 2016. ‘Inequalities in Open Source Software Development: Analysis of Contributor’s Commits in Apache Software Foundation Projects’, PLoS ONE, 11(4): e0152976. https://dx.doi.org/10.1371/journal.pone.0152976
Un chien Andalou, 1929. Directed by Luis Buñuel. Paris: Les Grands Films Classiques.
Cilip, 2012. ‘Code of Professional Practice’. Accessed 2018-03-21 at https://c.ymcdn.com/sites/www.cilip.org.uk/resource/resmgr/CILIP/About_Us/who_we_represent/Code_of_Professional_Practic.pdf
Claburn, T., 2007. ‘Google Releases Improved MySQL Code’, InformationWeek. Archived on 2012-11-16. Accessed 2018-04-12 at https://web.archive.org/web/20121116193838/http://www.informationweek.com/google-releases-improved-mysql-code/199201237
Clark, I., 2016. ‘The digital divide in the post-Snowden era.’ Journal of radical librarianship, 2, https://www.journal.radicallibrarianship.org/index.php/journal/article/view/12
Cole, J., 2011. ‘Big and Small Data at @Twitter’, presentation delivered on 2011-04-14 at O’Reilly MySQL Conference & Expo 2011 in Santa Clara, USA. Accessed 2018-04-12 at https://www.youtube.com/watch?v=5cKTP36HVgI
Doolin, B., 1998. ‘Information technology as disciplinary technology: being critical in interpretive research on information systems’, Journal of information technology, 13: 301-311.
Dryden, A., 2013. ‘The ethics of unpaid labor and the OSS community’, Ashe Dryden, Accessed 2018-03-26 at https://www.ashedryden.com/blog/the-ethics-of-unpaid-labor-and-the-oss-community
Earney, L., 2018. ‘National license negotiations advancing the OA transition: a view from Sweden and the UK’, presentation delivered on 2018-04-09 at UKSG 41st Annual Conference and Exhibition in Glasgow, UK.
Foucault, M., 1975/1991. Discipline and punish: the birth of the prison. Translated from French by Alan Sheridan. London: Penguin Books.
Galvan, A., 2016. ‘Architecture of Authority,’ Angela fixes things. Accessed 2018-03-23 at https://asgalvan.com/2016/12/05/architecture-of-authority/
Geek Feminism Wiki. ‘Richard Stallman’, Geek Feminism Wiki. Accessed 2018-04-21 at http://geekfeminism.wikia.com/wiki/Richard_Stallman
hooks, b., 2009. Reel to real: race, class and sex at the movies. New York City: Routledge.
Innovative Interfaces Inc., 2016a. ‘The Open Library Experience’, Innovative Interfaces Inc.. Accessed 2017-01-21 at https://www.iii.com/solutions/open-library-experience
Innovative Interfaces Inc., 2016b. ‘Sierra’, Innovative Interfaces Inc.. Accessed 2017-01-21 at https://www.iii.com/products/sierra
Kriss, J., 2016. ‘Anti-capitalist human scale software (and why it matters)’, Medium. Accessed 2017-01-13 at https://medium.com/@jkriss/anti-capitalist-human-scale-software-and-why-it-matters-5936a372b9d#.f6ml8gkuv
Lawson, S., 2018. ‘An ethics of care: what kind of open access do we want?’, presentation delivered on 2018-03-16 at RLUK Conference 2018 in London, UK https://youtu.be/3-CRzx6Y6QI
Lawson, S., Sanders, K., & Smith, L., 2015. ‘Commodification of the Information Profession: A Critique of Higher Education Under Neoliberalism’, Journal of librarianship and scholarly communication, 3(1): eP1182, https://dx.doi.org/10.7710/2162-3309.1182
Možnosti dialogu, 1982. Directed by Jan Švankmajer. Prague: Krátký Film Praha.
Neary, M., and Winn, J., 2012. ‘Open education: Common(s), commonism and the new common wealth’, Ephemera, 12(4), pp. 404-422.
Netcraft, 2016. ‘July 2016 Web Server Survey’, Netcraft. Accessed 2018-04-12 at https://news.netcraft.com/archives/2016/07/19/july-2016-web-server-survey.html
Norris, V., 2007. ‘’Interior Logic’: The Appropriate and Incorporation of Popular Surrealism into Classical American Animation’ in: Harper, G. and Stone, R., eds., 2007. The unsilvered screen: Surrealism on film. London: Wallflower Press, pp. 72-89.
Open Knowledge International. ‘Open Definition 2.1’, Open Definition. Accessed 2018-04-12 at https://opendefinition.org/od/2.1/en/
Open Source Initiative, 2007. ‘The Open Source Definition’, Open Source Initiative. Accessed 2018-04-12 at https://opensource.org/osd
Open Source Initiative, 2009. ‘OSI Board Meeting Minutes, Wednesday, March 4, 2009’, Open Source Initiative. Accessed 2018-04-12 at https://opensource.org/minutes20090304
Oracle. ‘MySQL Customer: YouTube’, MySQL. Accessed 2018-04-12 at https://www.mysql.com/customers/view/?id=750
Popowich, S., 2018. ‘“Ruthless Criticism of All that Exists”: Marxism, Technology, and Library Work’ in: Nicholson, K. J. and Seale, M., eds., 2018. The politics of theory and the practice of critical librarianship. Sacramento: Library Juice Press, pp. 39-66.
Reidsma, M., 2016. ‘Algorithmic Bias in Library Discovery Systems’, Matthew Reidsma. Accessed 2018-03-23 at https://matthew.reidsrow.com/articles/173
Rich, A., 1971. ‘The Burning of Paper Instead of Children’ in: Rich, A., 1971. The will to change: poems 1968-1970. London: W. W. Norton & Company, pp. 15-18.
Rogaway, P., 2015. ‘The Moral Character of Cryptographic Work’, paper delivered on 2015-12-02 at Asiacrypt 2015 in Auckland, New Zealand. Accessed 2018-04-12 at http://web.cs.ucdavis.edu/~rogaway/papers/moral-fn.pdf
Schneier, B., 1999. ‘Crypto-Gram’, Schneier on security. Accessed 2018-03-26 at https://www.schneier.com/crypto-gram/archives/1999/0915.html
Sélavy, V., 2018. ‘The beginnings of Surrealist cinema’, lecture delivered on 2018-03-05 at Close-Up Film Centre in London, UK.
Spellbound, 1945. Directed by Alfred Hitchcock. USA: Selznick International Pictures, Vanguard Films.
Watters, A., 2012. ‘Openwashing: n., having an appearance of open-source and open-licensing for marketing purposes, while continuing proprietary practices.’ Tweet published 2012-03-26, https://twitter.com/audreywatters/status/184387170415558656